How to Share Files Securely in 2026 (COMPLETE GUIDE)
In an era where data breaches cost companies an average of $4.45 million per incident and cyber attacks have increased by 44% globally, knowing how to share files securely isn't just good practice—it's essential for protecting your business and personal information. Whether you're sharing financial documents, legal contracts, client information, or intellectual property, every file transfer represents a potential security vulnerability.
Recent studies reveal that 83% of data breaches involve access to unprotected files, while 65% of data leaks stem from improperly shared documents. With remote work and digital collaboration becoming the norm, secure file sharing has evolved from a convenience to a critical security requirement. This comprehensive guide will show you the most effective methods to share files securely, protect sensitive information, and maintain complete control over your documents.
Quick Overview of Secure File Sharing Methods
- Papermark Secure Links: Password-protected, trackable links with advanced security features
- Encrypted Cloud Storage: Secure file sharing through encrypted cloud platforms
- Secure Data Rooms: Protected spaces for sharing multiple sensitive documents
- Email Encryption: Encrypted attachments for confidential email communications
- Secure File Transfer Services: Specialized platforms for large file transfers
Secure File Sharing Methods Compared
Before diving into the step-by-step instructions, here's a comparison to help you choose the best method for your needs:
Method 1: Using Papermark for Secure File Sharing
Papermark provides the most comprehensive and secure solution for sharing sensitive files, offering enterprise-grade security features combined with detailed tracking and analytics.
Step-by-step guide for Papermark secure file sharing:
-
Create your Papermark account:
- Visit Papermark
- Sign up for a free account or log in if you already have one
- Access your secure dashboard
-
Upload your sensitive file:
- Click "Upload Document" or drag and drop your file
- Papermark supports PDFs, presentations, spreadsheets, and more
- Wait for the upload to complete and file processing
![]()
- Configure security settings:
- Navigate to the document settings tab
- Enable password protection and set a strong, unique password
- Toggle email verification to require recipients to verify their identity
- Set access expiration dates to limit how long the file remains accessible
![]()
- Set advanced protection (optional):
- Enable dynamic watermarking to add recipient information to each page
- Toggle download prevention to allow viewing only (no downloads)
- Configure screenshot protection to discourage unauthorized captures
- Set custom permissions for different recipients

-
Generate and share secure link:
- Click "Share" to generate a unique, secure link
- Copy the link to share via email or messaging
- Share the password separately through a different communication channel
- Optionally, send the link directly through Papermark's built-in email system
-
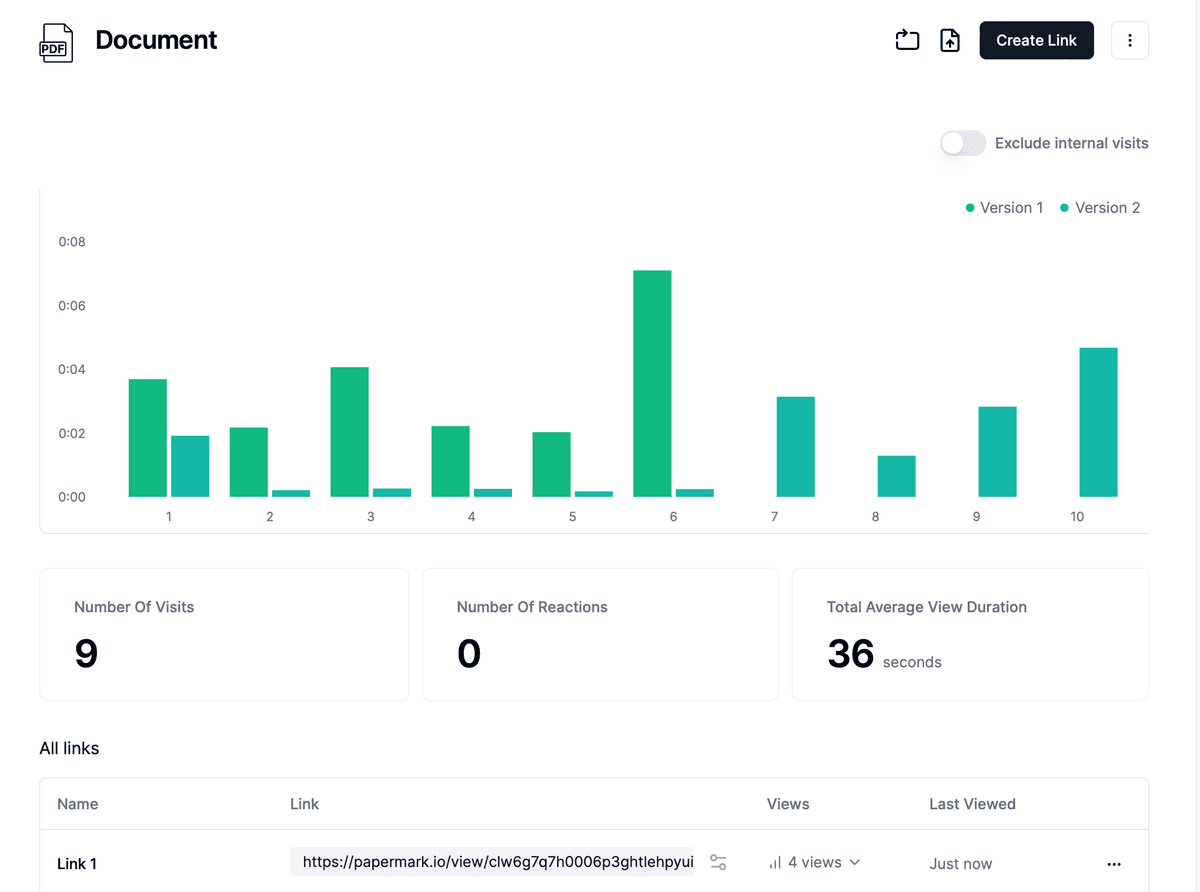
Monitor access and activity:
- Return to your dashboard to view real-time analytics
- See who accessed your file, when, and for how long
- Track which pages were viewed and how much time was spent on each
- Receive notifications when your file is accessed

- Revoke access if needed:
- Access your document settings at any time
- Disable the link to immediately revoke all access
- Change passwords to refresh security
- Update expiration dates or permissions as needed
Method 2: Encrypted Cloud Storage
Cloud storage platforms with encryption features provide a balance between accessibility and security for file sharing.
Step-by-step guide for encrypted cloud storage:
-
Choose a secure cloud platform:
- Select a provider with end-to-end encryption (pCloud, Tresorit, or Sync.com)
- Create an account with a strong, unique password
- Enable two-factor authentication (2FA) for added security
-
Upload your files securely:
- Ensure the upload connection is encrypted (look for HTTPS)
- Upload files to a dedicated secure folder
- Organize sensitive files separately from general documents
-
Configure sharing settings:
- Right-click the file and select "Share" or "Get Link"
- Enable password protection if available
- Set link expiration dates (typically 7-30 days)
- Choose view-only or download permissions
-
Share the encrypted link:
- Copy the generated secure link
- Send the link to recipients via email
- Share the password through a separate channel (SMS, phone call)
- Inform recipients about the expiration date
-
Monitor and manage access:
- Check sharing settings regularly
- Disable links when no longer needed
- Review access logs if available
- Update passwords periodically
Limitations: Most cloud storage platforms lack detailed analytics, advanced access controls, and custom watermarking features that specialized secure sharing platforms provide.
Method 3: Secure Data Rooms for Multiple Files
When sharing multiple sensitive documents with various stakeholders, a secure data room provides organized, controlled access.
Step-by-step guide for creating a secure data room:
- Set up your data room in Papermark:
- Log into your Papermark account
- Click "Create Data Room" from your dashboard
- Name your data room (e.g., "Q4 Financial Review" or "Client Project Files")

-
Organize your documents:
- Create folders for different document categories
- Upload multiple files at once using drag-and-drop
- Organize files logically (e.g., Legal, Financial, Technical)
- Add document descriptions or notes for clarity
-
Configure data room security:
- Set overall data room password protection
- Enable email verification for all visitors
- Configure watermarking to display viewer information
- Set expiration dates for the entire data room
-
Customize access permissions:
- Create different access levels for various recipients
- Assign folder-specific permissions
- Control which users can download vs. view only
- Set individual document passwords if needed
-
Share your secure data room:
- Generate a unique access link for the data room
- Send invitations to authorized users
- Provide access credentials securely
- Set up welcome messages or instructions
-
Track comprehensive analytics:
- Monitor which documents are accessed most frequently
- See detailed viewer engagement metrics
- Track time spent on each document
- Identify which sections receive the most attention
Method 4: Email Encryption for Secure Attachments
For quick, secure file sharing through email, encryption tools provide an additional security layer.
Step-by-step guide for encrypted email attachments:
-
Choose an encryption method:
- Use email client built-in encryption (Outlook, Gmail)
- Install encryption software (GPG, ProtonMail)
- Consider secure email services with automatic encryption
-
Encrypt your attachment:
- Use file encryption software before attaching
- Password protect the file using compatible software
- Create an encrypted ZIP archive of the file
- Verify the file is properly encrypted before sending
-
Compose your secure email:
- Enable email encryption in your email client
- Attach the encrypted file
- Keep attachment sizes reasonable (under 25MB for most providers)
- Write clear instructions for accessing the file
-
Share decryption credentials:
- Send the password through a different channel
- Use SMS, phone call, or secure messaging app
- Never include passwords in the same email as the attachment
- Provide clear decryption instructions
Note: Email encryption can be complex for non-technical users and lacks the tracking and control features of dedicated secure sharing platforms.
Method 5: Secure File Transfer Services
For large files that exceed email attachment limits, secure file transfer services provide temporary secure storage.
Step-by-step guide for secure file transfer services:
-
Select a secure transfer service:
- Choose reputable services like Internxt Send, Firefox Send alternatives
- Verify the service offers encryption and password protection
- Check maximum file size limits and storage duration
-
Upload your file securely:
- Visit the service website (ensure HTTPS connection)
- Upload your file using the provided interface
- Wait for the upload to complete and encryption to process
-
Configure security options:
- Set a strong password for file access
- Choose download limits (e.g., max 5 downloads)
- Set expiration time (24 hours to 7 days)
- Enable notifications for downloads if available
-
Share the download link:
- Copy the generated unique link
- Send to recipients via email or messaging
- Share password through separate communication
- Inform recipients about link expiration
-
Verify transfer completion:
- Confirm recipients successfully downloaded the file
- Delete the file from the service once transfer is complete
- Check for download notifications or confirmations
Limitations: File transfer services typically provide temporary storage only and lack comprehensive access controls, detailed analytics, and long-term document management features.
Best Practices for Secure File Sharing
Follow these essential practices to maximize file sharing security:
Password Management:
- Use unique, strong passwords for each shared file
- Combine letters, numbers, and special characters (minimum 12 characters)
- Never share passwords in the same communication as the file link
- Use password managers to generate and store complex passwords
- Change passwords immediately if you suspect compromise
Access Control:
- Apply the principle of least privilege (grant minimum necessary access)
- Regularly review and update access permissions
- Remove access for users who no longer need it
- Set appropriate expiration dates for time-sensitive documents
- Use email verification to confirm recipient identities
Communication Security:
- Share links and passwords through different channels
- Verify recipient identity before sharing sensitive files
- Use secure communication channels (encrypted messaging, phone calls)
- Confirm successful file receipt with recipients
- Provide clear instructions for accessing protected files
Monitoring and Compliance:
- Regularly review access logs and analytics
- Set up alerts for suspicious access attempts
- Maintain audit trails for compliance requirements
- Document all file sharing activities for sensitive documents
- Review and update security policies quarterly
File Preparation:
- Remove metadata and hidden information before sharing
- Use appropriate file formats (PDF for read-only documents)
- Apply watermarks to discourage unauthorized distribution
- Encrypt files before uploading to any platform
- Verify file integrity after uploading
Platform Selection:
- Choose platforms with proven security track records
- Verify encryption standards (AES-256 minimum)
- Ensure compliance with relevant regulations (GDPR, HIPAA, SOC 2)
- Check for security certifications and audits
- Read privacy policies and terms of service carefully
Key Takeaways
- Secure file sharing is essential in 2026, with 83% of data breaches involving unprotected files
- Papermark offers the most comprehensive solution with password protection, tracking, and dynamic watermarking
- Always use encryption, strong passwords, and separate communication channels for credentials
- Implement access expiration dates and monitor file access through detailed analytics
- Choose sharing methods based on sensitivity level, file size, and compliance requirements
- Regular security audits and access reviews are critical for maintaining document security
Conclusion
Sharing files securely requires a combination of the right tools, best practices, and ongoing vigilance. While various methods exist for secure file sharing, Papermark stands out as the most comprehensive solution, offering enterprise-grade security features, detailed analytics, and user-friendly controls that make protecting sensitive documents effortless.
Whether you're sharing confidential business documents, client information, financial records, or intellectual property, implementing proper security measures isn't optional—it's a critical business necessity. By following the methods outlined in this guide and choosing the right platform for your needs, you can significantly reduce the risk of data breaches while maintaining seamless collaboration.
Start protecting your sensitive files today with Papermark's advanced security features and gain complete visibility into how your documents are accessed and used.