Sharing confidential documents securely is a critical concern for businesses and individuals alike. With data breaches increasing by 70% in the past year and 82% of companies reporting unauthorized access to sensitive documents, choosing the right method for sharing confidential information has never been more important. Whether you're sharing legal contracts, financial statements, or intellectual property, this comprehensive guide will show you the best way to send confidential documents while maintaining security and control.
For organizations handling confidential client information, using a secure document sharing platform is essential to maintaining trust and preventing potentially devastating data leaks.
4 methods for secure confidential document sharing compared
| Security Method | Security Level | Ease of Use | Tracking Capabilities | Best For |
|---|---|---|---|---|
| Papermark Protection | Enterprise-Grade | High | Comprehensive | Business documents, sensitive data, professional sharing |
| Encrypted Email | Basic | Medium | Limited | One-time sharing, lower-sensitivity documents |
| Password-Protected PDFs | Moderate | Medium | None | Email transmission, basic security |
| Cloud Storage Security | Varies | Medium | Limited | Team collaboration, medium security |
Here are four effective methods for sending your confidential documents securely, from basic email encryption to advanced enterprise-level protection:
Method 1: Secure confidential documents with Papermark
Papermark offers enterprise-grade security for your confidential documents with advanced protection features. Follow this comprehensive step-by-step process to implement the highest level of security for your sensitive information:
Step 1: Create your secure environment
- Visit papermark.com and create your free account
- Access your secure dashboard
- Set up your secure workspace
- Configure your security preferences
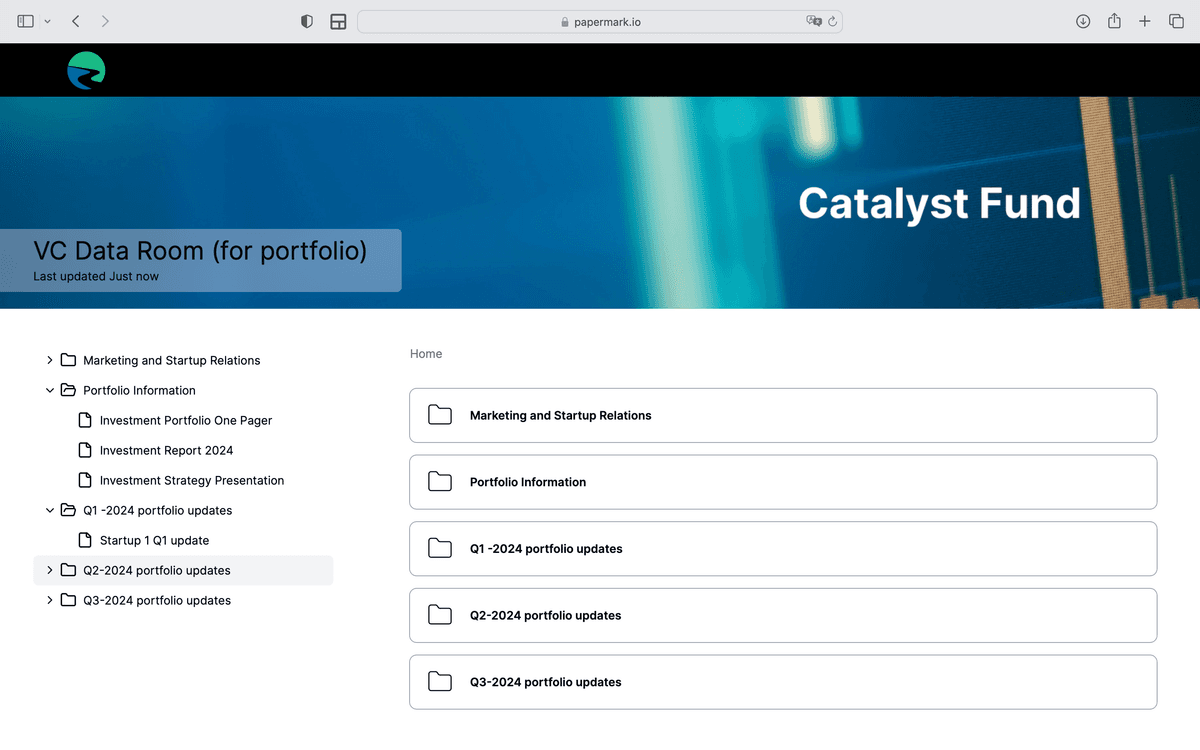
Step 2: Upload and secure your confidential documents
- Click Upload and select your confidential documents
- Wait for the files to process
- Access the file settings
![]()
Step 3: Configure protection settings
- Enable Password Protection
- Set a strong password
- Configure additional security options:
- Email verification requirement
- Download restrictions
- Expiration date
- Watermarking
- Viewer information collection

Step 4: Share securely
- Generate a secure sharing link
- Set permissions for recipients
- Send the link through your preferred channel
- Recipients will need to enter the password to access
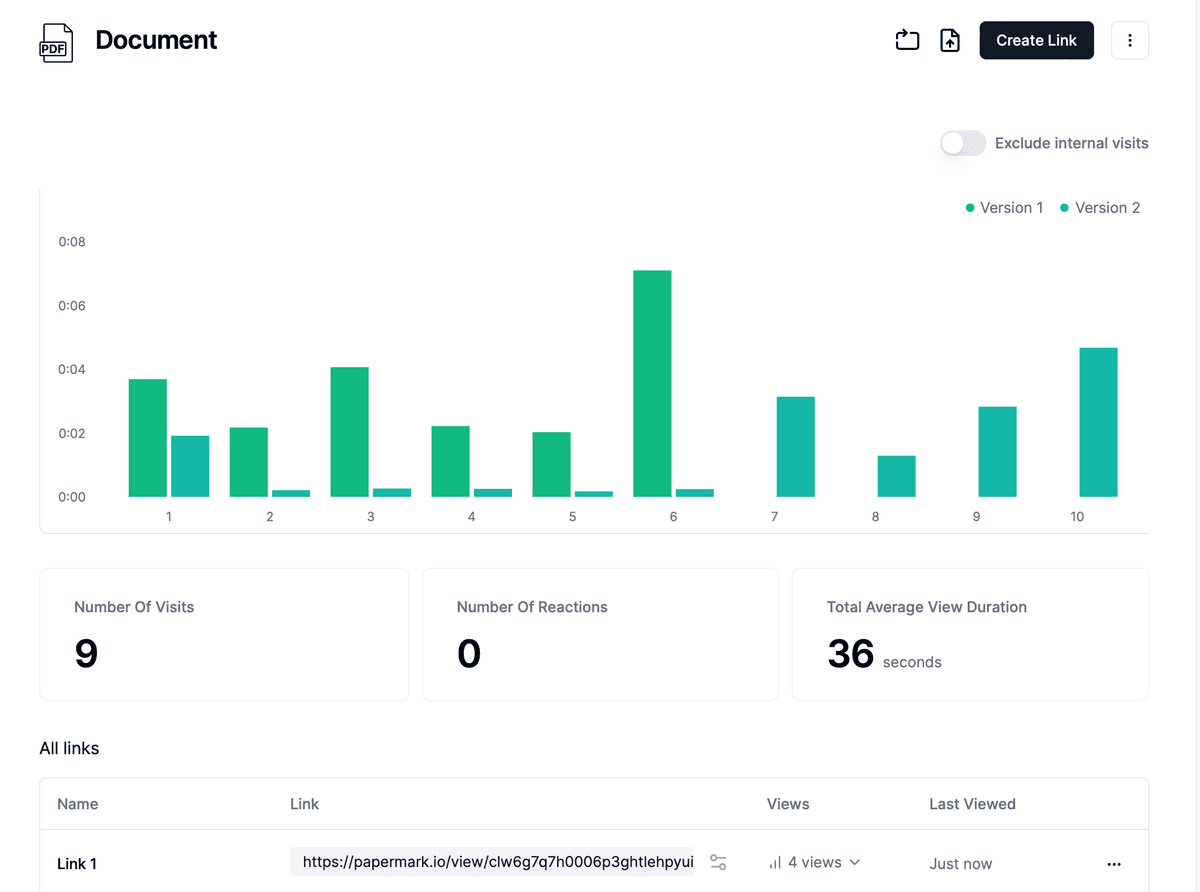
Step 5: Monitor access
- Track who views your confidential documents
- See when and for how long they viewed them
- Monitor any download attempts
- Receive notifications about access events
Advanced security features for confidential documents:
| Security Feature | Description |
|---|---|
| Secure Data Rooms | Create dedicated spaces for all your confidential documents with controlled access |
| Real-time Access Control | Instantly grant or revoke access to specific individuals |
| Expiration Settings | Set time-limited access to your confidential documents |
| Activity Tracking | Monitor who views your files and when |
| Email Verification | Require email verification before access |
| Custom Access Requirements | Request viewer information before granting access |
| Dynamic Watermarking | Automatically add viewer information to documents to discourage unauthorized sharing |
| View-Only Mode | Set files to view-only with download restrictions |
Papermark's security goes beyond simple password protection, offering comprehensive document security that maintains the integrity and confidentiality of your sensitive information.
Method 2: Email encryption and password protection
Standard email is not secure for sending sensitive confidential information. However, with proper encryption and secure email services, you can add a basic layer of security:
How to send confidential documents via encrypted email:
- Sign up for a secure email service (ProtonMail, Tutanota, or Virtru)
- Enable end-to-end encryption features in your email client
- Draft a new email to your recipient
- Attach your confidential documents directly to the encrypted email
- Set an encryption password or PIN that only the recipient knows
- Send the encrypted email through the secure service
- Share the decryption password separately (via phone call or text message)
- Request confirmation of receipt
Additional email security measures:
| Security Measure | Description |
|---|---|
| S/MIME or PGP Encryption | For advanced users, implement email encryption protocols |
| Two-Factor Authentication | Secure your email account with 2FA to prevent unauthorized access |
| Encrypted Attachments | If your email service doesn't offer end-to-end encryption, use encrypted ZIP files |
| Verify Recipient Information | Double-check email addresses before sending sensitive documents |
| Set Expiration Dates | Use email services that allow messages to expire after a certain period |
| Limit Retention Period | Request that recipients delete the documents after processing |
While email encryption provides basic protection, it lacks comprehensive tracking capabilities and depends on recipients following proper security protocols. For professional document sharing or highly sensitive materials, consider more robust solutions.
Method 3: Password-protected PDFs and encrypted files
Converting confidential documents to password-protected PDFs provides a moderate level of security:
- Scan or convert your confidential documents to PDF format
- Open the PDF in Adobe Acrobat or similar software
- Go to File > Protect > Encrypt with Password
- Set a strong password (combination of letters, numbers, and special characters)
- Configure permissions (restrict editing, printing, etc.)
- Save the encrypted PDF
- Share the password separately from the document
This method is relatively straightforward but lacks tracking capabilities and depends on the recipient maintaining proper security practices.
Method 4: Cloud storage security for confidential documents
Cloud storage services offer varying levels of security for your confidential documents, making them suitable for collaboration with trusted parties:
- Choose a secure cloud storage provider (Google Drive, Dropbox Business, Microsoft OneDrive, etc.)
- Upload your confidential documents to the cloud platform
- Configure sharing settings:
- Set specific user permissions (read-only recommended)
- Enable password protection if available
- Set expiration dates for shared links
- Enable two-factor authentication on your cloud account
- Regularly audit access logs to monitor who has viewed your documents
Benefits of cloud storage:
- Automatic backup and version history
- Controlled sharing with specific individuals
- Access from multiple devices
- Some file activity tracking
However, cloud storage typically offers limited tracking capabilities compared to specialized solutions like Papermark, and security features vary significantly among providers.
Comparison of confidential document sharing methods
| Feature | Email Attachments | Consumer Cloud Storage | Enterprise Solutions | Papermark |
|---|---|---|---|---|
| End-to-end encryption | ❌ | ⚠️ Limited | ✅ | ✅ |
| Password protection | ❌ | ⚠️ Basic | ✅ | ✅ |
| Access controls | ❌ | ⚠️ Limited | ✅ | ✅ |
| Document tracking | ❌ | ❌ | ⚠️ Limited | ✅ |
| Expiration settings | ❌ | ❌ | ⚠️ Limited | ✅ |
| Custom branding | ❌ | ❌ | ⚠️ Limited | ✅ |
| Dynamic watermarking | ❌ | ❌ | ⚠️ Some | ✅ |
| Access revocation | ❌ | ⚠️ Limited | ⚠️ Limited | ✅ |
| Audit trail | ❌ | ❌ | ⚠️ Limited | ✅ |
| Data room capability | ❌ | ❌ | ✅ | ✅ |
| Cost | Free | Free-Low | High | Affordable |
Best practices for sharing confidential documents
- Use strong, unique passwords: Create complex passwords for protected documents
- Implement multi-factor authentication: Add extra security layers with email verification
- Set appropriate expiration dates: Ensure documents aren't accessible longer than needed
- Limit access to necessary parties only: Use allowlists to restrict who can view documents
- Use secure communication channels: Share access information through separate, secure methods
- Regularly review access logs: Monitor who has accessed confidential documents
- Update security settings: Maintain current security protocols as needs change
- Train team members: Educate everyone on proper confidential document handling
- Have a revocation plan: Be prepared to quickly revoke access if needed
Real-World Example: Secure Marketing Document Sharing
See how Medusa JS securely shares confidential marketing materials and sales documents while maintaining complete control and tracking:
Conclusion
Secure sharing of confidential documents is a critical aspect of protecting your business and personal information. Whether you use encrypted email, password-protected PDFs, cloud storage, or Papermark's advanced security platform, implementing proper protection measures ensures that your valuable information remains confidential and secure.
For professionals handling sensitive information from multiple sources, Papermark's comprehensive security features provide the ideal balance of protection, usability, and control. By following the methods outlined in this guide, you can significantly reduce the risk of data leaks and unauthorized access to your critical confidential documents.

