Which files do you need to encrypt? (2026 guide)
Not all files need encryption, but certain types of documents contain sensitive information that requires protection from unauthorized access. Whether you're handling personal financial records, business contracts, or confidential client data, understanding which files need encryption helps you prioritize security efforts and protect what matters most.

Encryption transforms your files into unreadable code that can only be decrypted with the correct password or key. While encrypting everything might seem like the safest approach, it's more practical to focus on files containing sensitive, confidential, or legally protected information. This guide helps you identify which files require encryption and explains why certain file types need protection more than others.
Quick recap of files that need encryption
- Financial documents: Bank statements, tax returns, credit card information, and investment records
- Legal documents: Contracts, wills, legal agreements, and court documents
- Medical records: Health information, medical history, insurance documents, and prescription records
- Business confidential files: Trade secrets, proprietary information, business plans, and financial projections
- Client and customer data: Personal information, contact details, and confidential client communications
- Intellectual property: Patents, research data, source code, and creative works
- Credentials and passwords: Password lists, API keys, security certificates, and authentication tokens
- Due diligence documents: Financial audits, compliance reports, legal reviews, and risk assessments
- Pitch decks and fundraising materials: Investor presentations, business proposals, and fundraising documents
- Mergers and acquisitions files: M&A agreements, valuation reports, integration plans, and deal documents
- Data room contents: Confidential business information shared during transactions, fundraising, or partnerships
1. Financial documents and records
Financial documents contain sensitive information about your income, assets, debts, and financial transactions. These files are prime targets for identity theft and financial fraud.
Types of files to encrypt:
- Bank statements and account information
- Tax returns and tax-related documents
- Credit card statements and payment information
- Investment account statements and portfolio information
- Loan documents and mortgage papers
- Insurance policies and claims information
- Pay stubs and employment income records
- Budget spreadsheets and financial planning documents
Why encryption matters: Financial documents reveal your complete financial picture, including account numbers, balances, and transaction history. Unencrypted financial files can be used to commit fraud, drain accounts, or steal your identity. Encryption protects this sensitive information from unauthorized access.
Best practices: Encrypt all financial documents before storing them digitally, use password-protected file sharing when sending financial information, and regularly review access logs if using cloud-based encryption services.
2. Legal documents and contracts
Legal documents often contain confidential information, binding agreements, and sensitive terms that should remain private. These files require encryption to protect both your legal rights and confidential information.
Types of files to encrypt:
- Legal contracts and agreements
- Wills and estate planning documents
- Divorce papers and family court documents
- Non-disclosure agreements (NDAs)
- Settlement agreements and legal correspondence
- Intellectual property licenses and agreements
- Employment contracts and severance agreements
- Real estate documents and property deeds
Why encryption matters: Legal documents contain binding terms, confidential negotiations, and sensitive personal information. Unauthorized access to these files could compromise legal positions, reveal confidential terms, or enable fraud. Encryption ensures that only authorized parties can access these critical documents.
Best practices: Encrypt legal documents before sharing with attorneys or other parties, use secure document sharing platforms with audit trails, and maintain encrypted backups of important legal files.
3. Medical records and health information
Medical records contain highly sensitive health information protected by privacy laws in many jurisdictions. These files require strong encryption to comply with regulations and protect patient privacy.
Types of files to encrypt:
- Medical records and health history
- Prescription records and medication lists
- Insurance documents and health insurance cards
- Lab results and diagnostic reports
- Mental health records and therapy notes
- Medical bills and healthcare payment information
- Health insurance claims and correspondence
Why encryption matters: Medical records contain sensitive health information that, if exposed, can lead to discrimination, insurance fraud, or identity theft. Many countries have strict regulations (like HIPAA in the United States) requiring protection of health information. Encryption helps ensure compliance and protects patient privacy.
Best practices: Use encryption for all medical records stored digitally, ensure any file sharing platform used for medical documents complies with health privacy regulations, and limit access to only authorized healthcare providers and patients.
4. Business confidential information
Business files containing proprietary information, trade secrets, or competitive intelligence require encryption to protect your company's competitive advantage and confidential operations.
Types of files to encrypt:
- Business plans and strategic documents
- Financial projections and budget information
- Trade secrets and proprietary formulas
- Customer lists and contact databases
- Vendor agreements and supplier contracts
- Employee information and HR records
- Marketing strategies and campaign plans
- Product development documents and roadmaps
Why encryption matters: Business confidential information, if exposed, can damage competitive position, reveal strategic plans, or compromise business relationships. Encryption protects trade secrets and proprietary information from unauthorized access, whether from competitors, disgruntled employees, or external threats.
Best practices: Implement encryption for all business confidential files, use secure data rooms for sharing sensitive business documents with investors or partners, and establish clear policies about which files require encryption.

5. Client and customer data
Files containing client or customer information require encryption to protect privacy, comply with data protection regulations, and maintain trust in your business relationships.
Types of files to encrypt:
- Customer contact information and databases
- Client communications and correspondence
- Customer service records and support tickets
- Client financial information and payment data
- Customer preferences and behavioral data
- Client contracts and service agreements
- Customer feedback and survey responses
Why encryption matters: Client and customer data is often protected by privacy regulations like GDPR, CCPA, or other data protection laws. Unauthorized access to this information can result in regulatory fines, legal liability, and loss of customer trust. Encryption helps ensure compliance and protects customer privacy.
Best practices: Encrypt all files containing customer data, use encrypted file sharing when sending customer information to authorized parties, and implement access controls to limit who can view encrypted customer files.
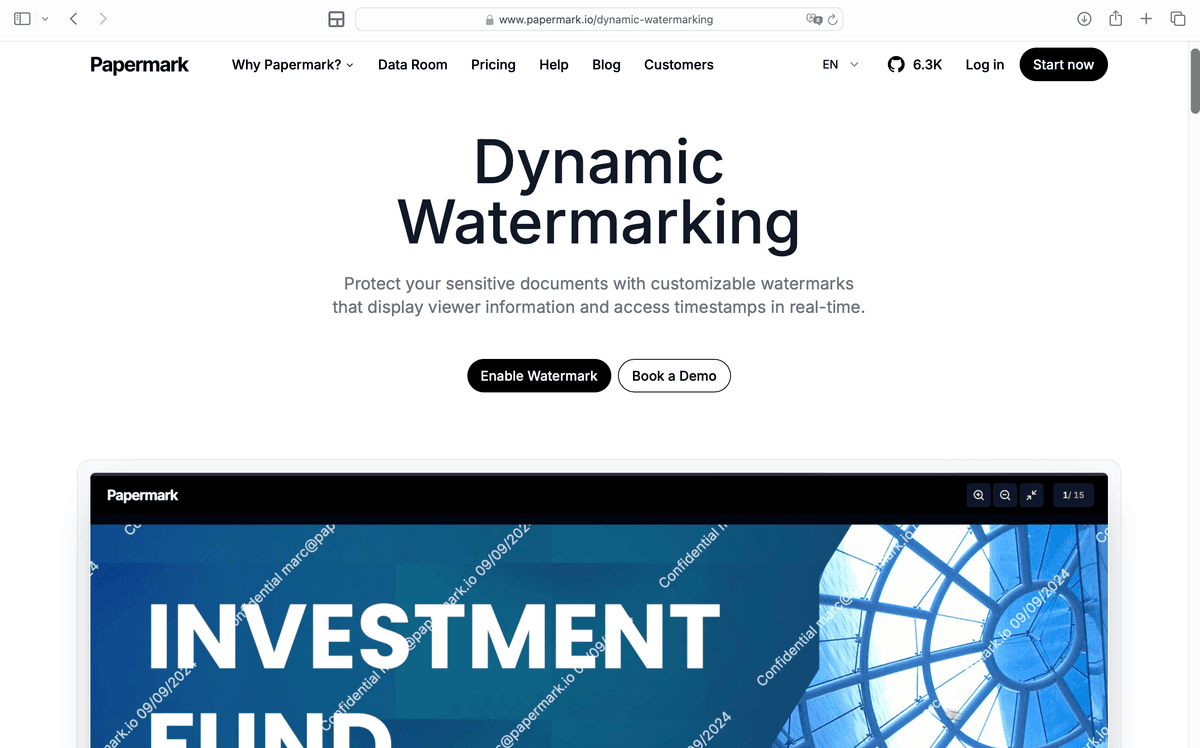
6. Intellectual property and creative works
Files containing intellectual property, research data, or creative works require encryption to protect your rights and prevent unauthorized use or theft of your work.
Types of files to encrypt:
- Source code and software development files
- Research data and experimental results
- Patent applications and technical specifications
- Creative works and artistic content
- Design files and architectural plans
- Product specifications and technical documentation
- Academic research and unpublished papers
Why encryption matters: Intellectual property represents significant value and investment. Unauthorized access to source code, research data, or creative works can lead to theft, plagiarism, or loss of competitive advantage. Encryption protects your intellectual property from unauthorized access and use.
Best practices: Encrypt all intellectual property files, especially when sharing with partners or collaborators, use secure document sharing with access controls and watermarks, and maintain encrypted backups of important intellectual property.
7. Credentials and authentication information
Files containing passwords, API keys, security certificates, or other authentication credentials require strong encryption to prevent unauthorized access to your accounts and systems.
Types of files to encrypt:
- Password lists and credential databases
- API keys and access tokens
- Security certificates and private keys
- SSH keys and encryption keys
- Database connection strings and credentials
- Service account passwords and authentication tokens
- Two-factor authentication backup codes
Why encryption matters: Credentials and authentication information provide access to your accounts, systems, and data. If these files are compromised, attackers can gain unauthorized access to your services, steal data, or cause significant damage. Encryption is essential for protecting these critical security files.
Best practices: Use strong encryption for all credential files, never store credentials in unencrypted files, use password-protected encryption with additional security features, and consider using dedicated password managers for credential storage.
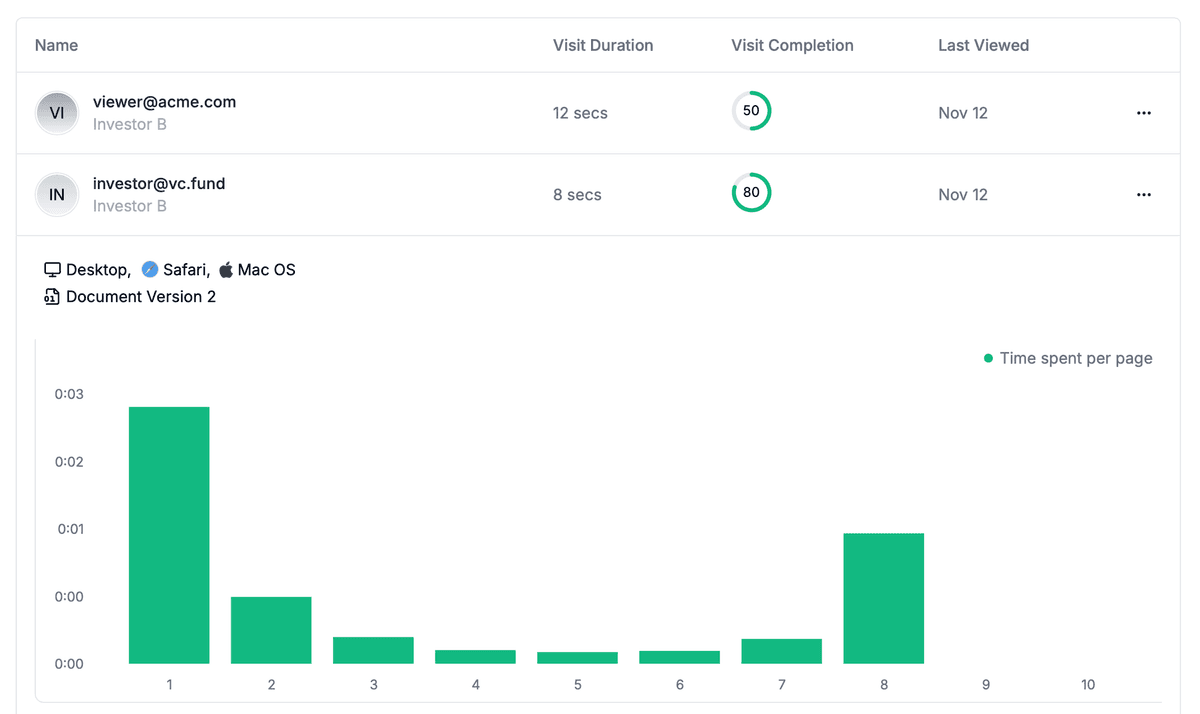
Best practices for file encryption
Understanding which files need encryption is the first step. Implementing proper encryption practices ensures your sensitive files remain protected.
-
Prioritize sensitive files: Focus encryption efforts on files containing financial information, legal documents, medical records, business confidential information, client data, intellectual property, or credentials.
-
Use strong encryption methods: Choose encryption methods that use AES-256 or stronger algorithms. For detailed guidance, see our guide on how to encrypt files using various methods.
-
Implement access controls: Combine encryption with access controls, password protection, and secure file sharing features to create multiple layers of security.
-
Regular security reviews: Periodically review which files you have encrypted and ensure all sensitive files are properly protected. Update encryption methods as security standards evolve.
-
Secure file sharing: When sharing encrypted files, use secure platforms that maintain encryption during transmission and provide access controls, audit trails, and tracking capabilities.
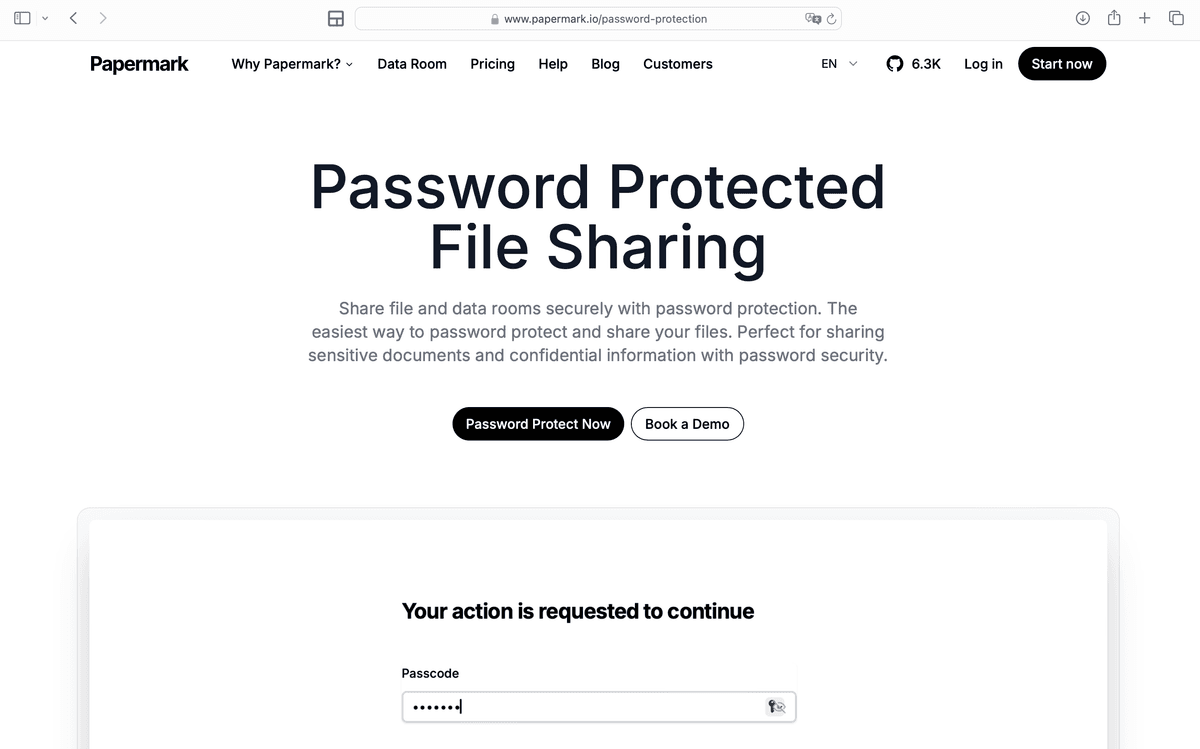
- Backup encrypted files: Maintain encrypted backups of important files, ensuring that backup copies are also encrypted and stored securely.
Conclusion
Not all files need encryption, but files containing financial information, legal documents, medical records, business confidential information, client data, intellectual property, or credentials should always be encrypted. Understanding which files require protection helps you prioritize security efforts and protect sensitive information from unauthorized access.
When encrypting files, choose strong encryption methods, implement access controls, and use secure sharing platforms that maintain encryption throughout the file lifecycle. For comprehensive file encryption with advanced security features, consider using platforms like Papermark that combine encryption with password protection, access controls, and detailed analytics.